TL;DR – Passkeys explained. They’re phishing-proof, can’t be reused across sites, and remove the need to remember complex strings — but interoperability and limited adoption still hold them back. Once every major ecosystem supports them, passkeys won’t just replace passwords; they’ll quietly end them.
A long time ago, a poor woodcutter named Ali Baba found a cave used by forty thieves to store their loot. It was guarded with the worst security system ever. A secret phrase: “Open sesame”.
We all know what happened next. Ali Baba overheard it when the thieves used it. His brother overheard it when he used it and a lot of things happened.
Over the years, we and our technology have transformed in unimaginable ways. Our security systems have become far more advanced than ever. And yet, one aspect remains unchanged. Our generations-old tradition of using weak passwords. Even after all the guidelines and multiple painful breaches around the world, this is one tradition that we just can’t shake off.
The recent Louvre heist investigation has brought some alarming revelations to light. Examining the audit records of 2014, the investigators found that the security password of the museum was recorded as “LOUVRE”. I can’t personally confirm whether the thieves used this password or not, but it’s speculated that this password has remained unchanged over the years and was the same at the time of the heist.
Nevertheless, it’s very alarming and equally shocking that a museum named Louvre housing priceless artifacts and paintings from around the world, would ever use “LOUVRE” as its password.
Research shows that people are aware of the correct practices of creating good passwords but choose not to. The reason is convenience. Today we use hundreds of accounts at work and at home. To remember or make unique passwords for each is very inconvenient. Since the consequence of choosing a weak password is not immediate, convenience will always win over security.
But now, there’s nothing to worry. There is a new replacement in town. Something that can replace passwords with a simple four digit PIN, the passkeys. And guess what? It cannot be broken all that easily.
Wait, what now? Well, it’s more than just a four digit PIN.
What exactly is a Passkey?
When using passwords, we need to remember and enter an entire string of letters, numbers and special characters. These are hashed and sent to the server where the passwords are stored and compared. If it matches, then your identity is confirmed and you are given access. Passkeys don’t work this way. You don’t need to remember a complicated string to authenticate yourself. Sounds awesome, right?
Well, when a passkey is created, your device and the website or app set up a unique key pair – private key and public key. The private key is stored on your device and the public key is stored on the website’s or app’s server.
When you try to log in, the website sends a unique and random challenge to your device. Your device then signs it with your private key. This signed challenge is sent to the website, where it’s verified using your public key. If it checks out, you are logged in.
This way, your account is much safer. The private key always stays on your device. As a result, if the challenge is intercepted, there is no way anyone can figure out what your private key is.
Now you might have a doubt. If private and public keys exist, then why do you have the 4-digit PIN? Well, it’s just to unlock the part of your device where the private key is stored. This way, if someone breaches your phone, they can’t access the private key without the PIN. The 4-digit PIN can be substituted with your fingerprint or your face scans depending on the compatibility of your device.
Fast IDentity Online 2 (FIDO2)
The passkey system runs on an open standard called Fast Identity Online 2 (FIDO2). It is basically a password-less authentication standard. It was developed by the FIDO Alliance (industry group founded by Google, Microsoft, PayPal, Lenovo, Yubico, and others) and the W3C (World Wide Web Consortium) – a body that defines web standards like HTML and CSS.
FIDO2 is a bundle of two protocols
- WebAuthn (Web Authentication API) – This was created by W3C and allows websites to securely communicate with your browser.
- CTAP2 (Client to Authenticator Protocol 2) – This was created by the FIDO Alliance and helps the browser to securely communicate with your device’s authenticator.
How FIDO2 works (Together with WebAuthn and CTAP2)
During Registration
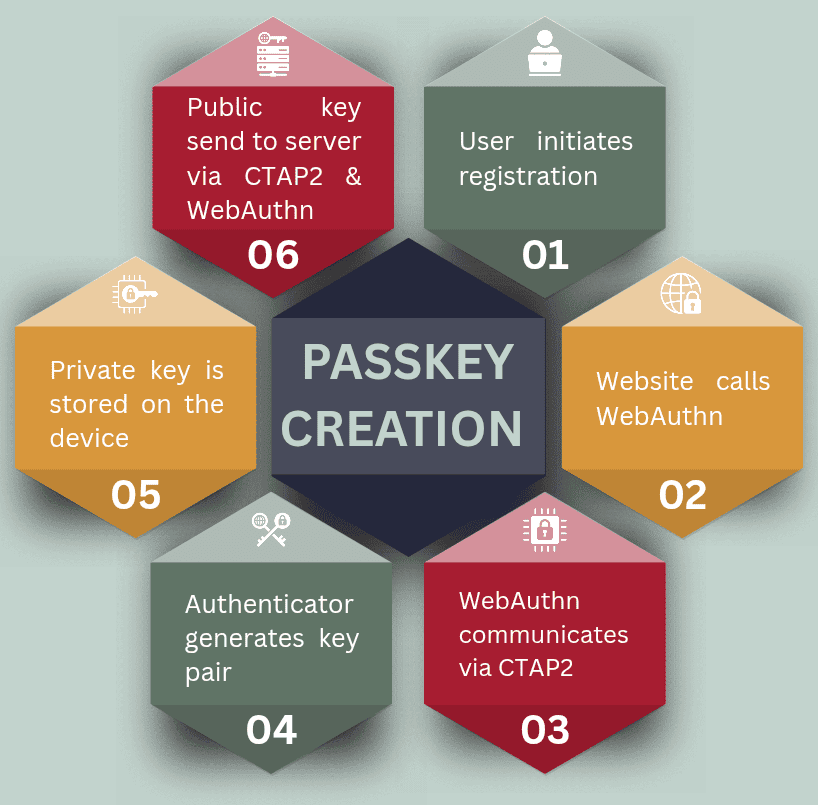
When we create an account in the site that supports passkeys, the website calls WebAuthn on our device to create new credentials for the user. WebAuthn passes the request to the device authenticator through CTAP2. The authenticator creates a new key pair. The private key is stored on the device while the public key is sent to the server via WebAuthn.
Logging in
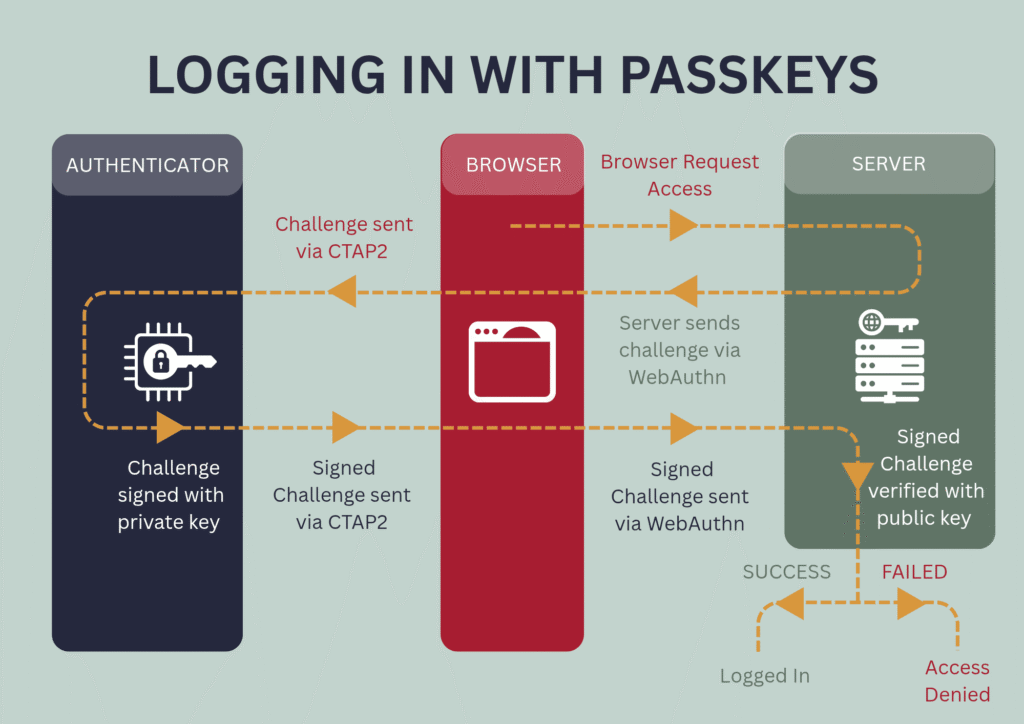
The website sends a random unique challenge to the WebAuthn. The WebAuthn passes it to the device authenticator through CTAP2. The authenticator signs the challenge with the private key and sends it back to the website through WebAuthn. The website then verifies the signed challenge with its public key. If the signed challenge check out, you are logged in. Otherwise, you are not signed in.
Advantages of Passkeys
- Phishing Proof Authentication – Phishing is a technique scammers use to create fake look-a-like forgot password or similar pages of well known services companies. We unsuspectedly enter our user id and password and the scammers can gain access to our account. Here since the private key remains on our device, there’s nothing basically for the user to share here. FIDO2 also ensures the request came from the original site and not from a duplicate. So it won’t sign any challenges from fake websites.
- Breach Proof – Many passwords are leaked through breaches in the company server. When breaches happen, usernames and passwords of millions of users are leaked by hackers and sold on the dark web. Here since the private key always remains on the device, during a breach the user data is protected.
- No credential Reuse – Usually users use the same password for multiple services. If the scammers gain access to one, they can infiltrate all the accounts of the user. In the case of passkeys, keys generated by different services are different by default.
- Intercepting doesn’t work – Intercepting old signed challenges are of no use because each time the website sends a unique new challenge. Past signed challenges wont help in logging in later.
- Hardware Backed Protection – Private keys live inside secure hardware (Secure Enclave on iOS, Titan M on Android, TPM on Windows). Malware or an app can’t read or copy them.
- Built-In Two-Factor Security – Passkey logins use your private key stored on your device and your face or your fingerprint or your PIN. Unlike password, these cannot be easily replicated by a scammer.
- Faster and Smoother Login – You are not required to remember big complicated strings. All you need to do is to scan your face or your fingerprint or enter a 4-digit PIN.
Disadvantages of Passkeys
- Ecosystem Lock-In – Passkey pairs are synced through each vendor’s respective clouds via end-to-end encryption to facilitate seamless access multiple devices. These encrypted passkey pairs are not transferable from one company ecosystem to another. You definitely would have faced this issue firsthand when you switched from an Android phone to an Apple phone or vice-versa. You would have to configure a different account for the new device. For example, passwords stored in the password manager of Google wouldn’t be accessible on Apple. This limits the users’ freedom to switch, and they end up upgrading to the devices in that particular ecosystem to avoid the hassle.
- Device Failure together with absence of cloud backup – Imagine a situation where your only signed in device stops working and you haven’t enabled any cloud backup. You would no longer be able to use the same account. You’ll have to create a new account from scratch.
Are Passkeys really bulletproof?
Imagine a situation where your only signed-in device is stolen by the hacker and the hacker somehow knows your 4-digit PIN. In this case he can gain access to your account easily and can enable it on other devices.
But don’t worry, there are safe practices you can follow to prevents such risks.
- Enable biometric unlock (finger print or face id )
- Keep another device always signed in to your account and also enable remote wipe option.
- Report and Remote wipe the device almost immediately when you realise it’s stolen.
Passkeys just a gimmick?
Passkeys don’t ask you to be smarter than hackers — they remove your weakness from the equation.
Safety of our passwords depends entirely on our intelligence or server security that no hacker can outsmart. We could always run into a smarter scammer who could confuse us and steal our credentials without us knowing or a smarter hacker could hack the system and steal the passwords.
The day passwords die will be quieter than we expect — replaced by a tap, a glance, or a fingerprint.
Passkeys take care of this as there is no shared secret. There nothing to type or even to reuse. But as of now, only few companies have adopted this technology. There is also a problem of interoperability. Once these are resolved, passkeys will quietly replace our passwords for good.
Rate this post
Drop a quick star rating — totally anonymous, and it helps me shape better articles.
FAQs
A passkey is a modern login credential that replaces passwords with a pair of cryptographic keys — one public, one private.The private key stays securely on your device, while the public key sits on the server. When you log in, your device signs a one-time challenge using the private key. This signed challenge is verified by the server using your public key. If it checks out, you are signed in.
No. The PIN or fingerprint doesn’t act as your passkey — it simply unlocks the secure area of your device where your private key is stored. The actual authentication happens by encryption, not your PIN.
Passkeys only work on the exact website or app where they were registered.If a hacker creates a fake login page, your browser refuses to send the authentication request — so your credentials can’t be stolen.
If you’ve enabled encrypted backup (like iCloud Keychain or Google Password Manager), your passkeys can be restored on a new device after verifying your account.Without a backup, recovery can be difficult or impossible — you’ll need to re-register passkeys on each service manually.
Highly unlikely. Passkeys are stored as end-to-end encrypted blobs. Even Apple, Google, or Microsoft can’t read them.However, if an attacker gains full control of your cloud account and is in possession of one of your signed devices and knows your PIN, they could restore your encrypted passkeys onto another trusted device. So, securing your cloud account with strong 2FA and activating biometrics is crucial.
Passkeys sync automatically within the same ecosystem (Apple, Google, or Microsoft).Cross-platform transfer — like moving from iCloud to Android — isn’t seamless yet. You’ll usually need to re-register or use a passkey-compatible password manager (like 1Password or Bitwarden).
Subscribe to our monthly newsletter
Liked what you read? Excellent. Then avoid the noble sport of “accidentally missing future posts.” We send a once-a-month, actually just one newsletter covering what’s been going on at Sentient Rant every month. No spam, no sudden “special offers,” no daily motivational wisdom—just a calm, curated summary of everything published that month. If you prefer technology explained without unnecessary jargon, subscribe and stay in the loop. One email. Once a month. That’s the entire deal.
Check out our posts
How VPNs really work: Protocols, safety and myth
The real cost of free apps
183 Million Gmail addresses in a data leak — Here’s what actually happened (and what you should do)
Brain-computer interfaces (BCI) : The next upgrade
How WhatsApp Uses the Signal Protocol (X3DH + Double Ratchet) Explained in Simple Words
DNA data storage: Replacing hard drives with DNA
Hard drives fade. DNA endures. Discover how scientists are turning life’s own…